
Table of Contents
Crypto wallet theft hit $494M. In 2024: A Growing Concern for Security
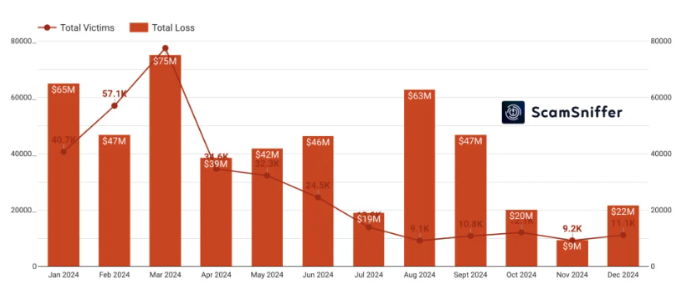
Last year, scammers targeted over 300,000 wallet addresses with wallet drainer assaults, stealing $494 million worth of cryptocurrency.
Even while the number of victims only increased by 3.7%, this is a 67% increase over 2023 figures, suggesting that victims often held larger amounts.
Web3 anti-scam platform ‘Scam Sniffer,’ which has been monitoring wallet drainer activity for some time and has previously reported attack waves that affected up to 100,000 users simultaneously, is the source of the data.
Phishing tools known as “wallet drainers” are made expressly to steal cryptocurrencies or other digital assets from users’ wallets; they are frequently used on phony or compromised websites.
30 large-scale (over $1 million) wallet drainer thefts were reported by Scam Sniffer in 2024, with the highest single crime cashing in $55.4 million worth of cryptocurrencies.
This happened early in the year, when phishing activity was spurred by increases in the price of Bitcoin. Wallet drainer assaults resulted in the theft of $187 million in the first quarter of this year.
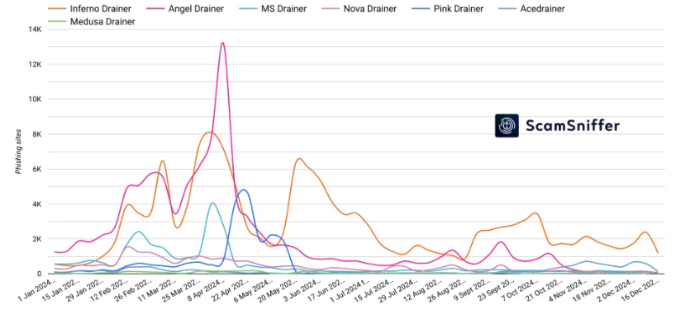
‘Pink Drainer,’ a well-known drainer service that was previously observed posing as journalists in phishing attempts to breach Discord and Twitter accounts for cryptocurrency-stealing assaults, announced its departure in the second quarter of this year.
Phishing activity decreased as a result, but in the third quarter, the scammers began to pick up speed. The Inferno service led the way, generating $110 million in damages in August and September alone.
Lastly, the activity slowed down in the year’s last quarter, which only contributed to roughly 10.3% of the overall losses in 2024. According to ScamSniffer, Acedrainer also became a significant player at that time, capturing 20% of the drainer market.
Stablecoins (33.5%) and staking (40.9%) were among the most targeted, while Ethereum (85.3%) had the largest losses, totaling $152 million.
Scam Sniffer identifies several trends for 2024, including a change in signature types that make money theft easier and the usage of phony CAPTCHA and Cloudflare pages, as well as IPFS, to avoid detection.
In particular, the majority of thefts used the’setOwner’ (31.9%) or ‘Permit’ signature (56.7%) to siphon off money. The second modifies the ownership or administrative rights of smart contracts, while the first authorizes token expenditure in accordance with the EIP-2612 standard.
Another significant trend is the rise in the use of Twitter and Google Ads to drive attention to phishing websites, where the attackers deploy bots, compromised accounts, and phony token airdrops.
It is advised to avoid Web3 attacks by only interacting with reputable and validated websites, verifying URLs with official project websites, reading permission requests and transaction approval prompts before signing, and simulating transactions before executing them.
Make careful to activate the built-in warnings for fraudulent or phishing transactions that many wallets provide. Lastly, make sure there are no questionable permissions active by using token revoking tools.
FAQ
The increase in crypto wallet theft, which totaled $494 million in 2024, was primarily driven by advancements in phishing tools like wallet drainers. These tools exploited vulnerabilities in websites and user behaviors. Additionally, rising cryptocurrency prices early in the year encouraged heightened phishing activity.
Wallet drainers are phishing tools designed to steal digital assets from users’ crypto wallets. They often operate through fake or compromised websites, tricking users into granting permissions or signing transactions that enable scammers to access and transfer funds from their wallets.
Ethereum faced the largest losses, accounting for 85.3% of stolen funds, amounting to $152 million. Other targeted assets included stablecoins (33.5%) and staking-related assets (40.9%), which were appealing due to their value and widespread use.
To avoid becoming a victim:
- Interact only with reputable and verified websites.
- Verify URLs with official project websites.
- Carefully review permission requests and transaction prompts before signing.
- Use wallet tools that provide phishing or fraud warnings.
- Employ token revoking tools to check and remove questionable permissions
Key trends include:
- Increased use of specific signature types like ‘setOwner’ and ‘Permit’ to facilitate theft.
- Adoption of fake CAPTCHA, Cloudflare pages, and IPFS to evade detection.
- Greater reliance on Twitter and Google Ads to direct users to phishing websites.
- Deployment of bots, compromised accounts, and fake token airdrops to lure victims.

